 The groundbreaking image encryption scheme can be applied in mobile encrypted payment and information anti-counterfeiting
The groundbreaking image encryption scheme can be applied in mobile encrypted payment and information anti-counterfeiting
A joint research team, formed by researchers of the University of Macau (UM), Wuhan University (WHU), Beijing Normal University (BNU), the University of Hong Kong (HKU), and the University of Birmingham (UB), has proposed a groundbreaking image encryption scheme that uses a single metasurface as a reusable generator of different keys to encode various secret images in a computational way. The study has been published online in Science Advances, a sub-publication of the prestigious international journal Science.
Information security is of great importance in all aspects of life, and the need for enhanced information security has spawned various encryption methods. In almost all encryption techniques, a piece of information or an image is first encrypted by secret keys into a ciphertext using a specific algorithm, and the information can only be decrypted correctly if all the keys, ciphertext, and algorithm used in encryption are obtained. Therefore, the encryption algorithm, as well as the presence and form of transmission of the keys and ciphertext are all critical to the security of an encryption scheme.
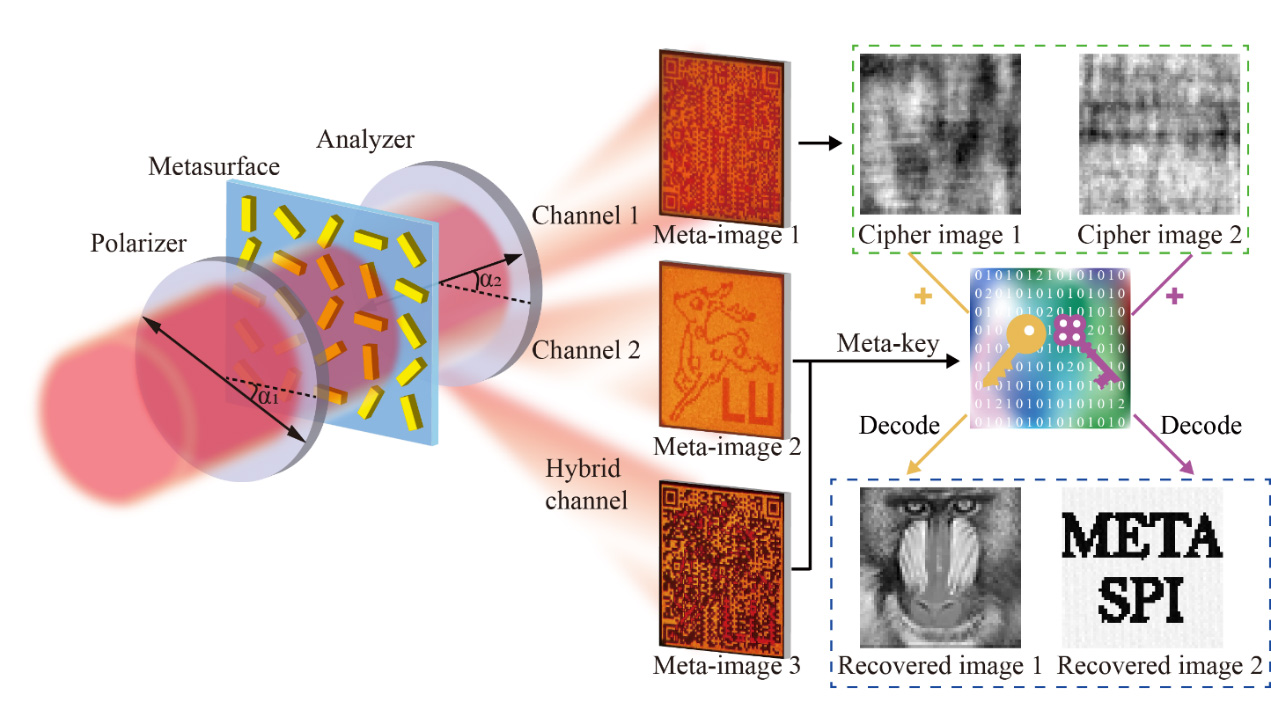
The research team creatively hid the keys and ciphertext in different images generated by a tiny piece of metasurface (<0.1*0.1 mm2), and used computational imaging algorithms to encrypt and decrypt different information and images. More importantly, in this scheme, a single metasurface can generate different keys by choosing different rules for different secret images, which effectively reduces the burden of massive data transmission and eliminates the possibility of digital data leakage that sometimes occurs with conventional encryption methods. Prof Liu Hongchao in UM’s Institute of Applied Physics and Materials Engineering (IAPME), and his research team, used a metasurface the size of a cross-section of a hair to generate a QR code, and by scanning the QR code, they obtained the ciphertext. According to Prof Liu, the QR code itself can generate different secret keys with different mathematical operations to complete the decryption process. One only needs a smart phone and a tiny metasurface to achieve the encryption and decryption of different secret images, which promises practical applications of metasurfaces such as mobile encrypted payment and information anti-counterfeiting.
Zheng Peixia, a doctoral student in the IAPME, is the first author of the study. Dai Qi and Li Zile at WHU are the co-first authors. Liu Hongchao, WHU professor Zheng Guoxing, and HKU chair professor Zhang Shuang are the co-corresponding authors. Prof. Xiong Jun and Ye Zhiyuan at BNU also made important contributions to the study. The study was funded by the Start-up Research Grant of UM (file name: SRG2019-00174-IAPME), the National Natural Science Foundation of China (file numbers: 91950110, 11774273, 11904267, 11474027, 11735005), and the Horizon 2020 initiative of the European Research Council (file numbers: 734578 D-SPA and 648783 TOPOLOGICAL).
The full text of the research article can be viewed at https://advances.sciencemag.org/content/7/21/eabg0363